Cybersecurity Resources & Projects
Practical tools, scripts, and real-world projects
Explore hands-on resources from my work in red teaming and penetration testing. From automation frameworks and recon scripts to complete security assessments, these resources are designed to accelerate your learning and give you practical, repeatable workflows. New labs and setup guides are coming soon.
Offensive Automation Tool
APT Framework
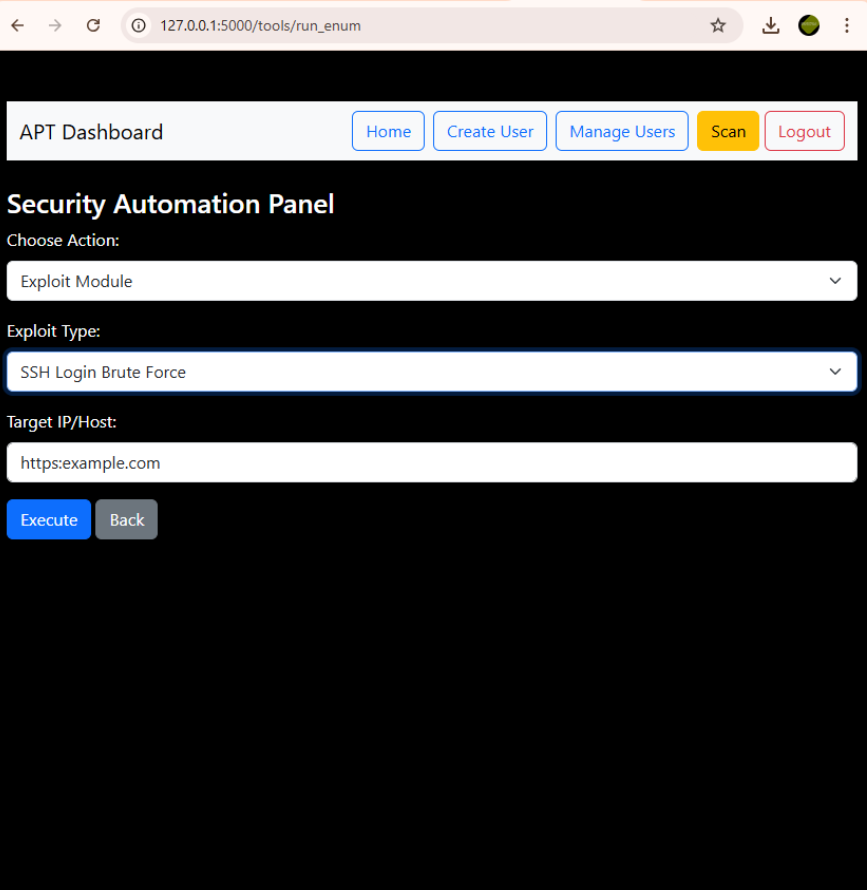
A modular red teaming framework designed to automate the entire attack lifecycle — from reconnaissance and vulnerability scanning to exploitation and reporting.
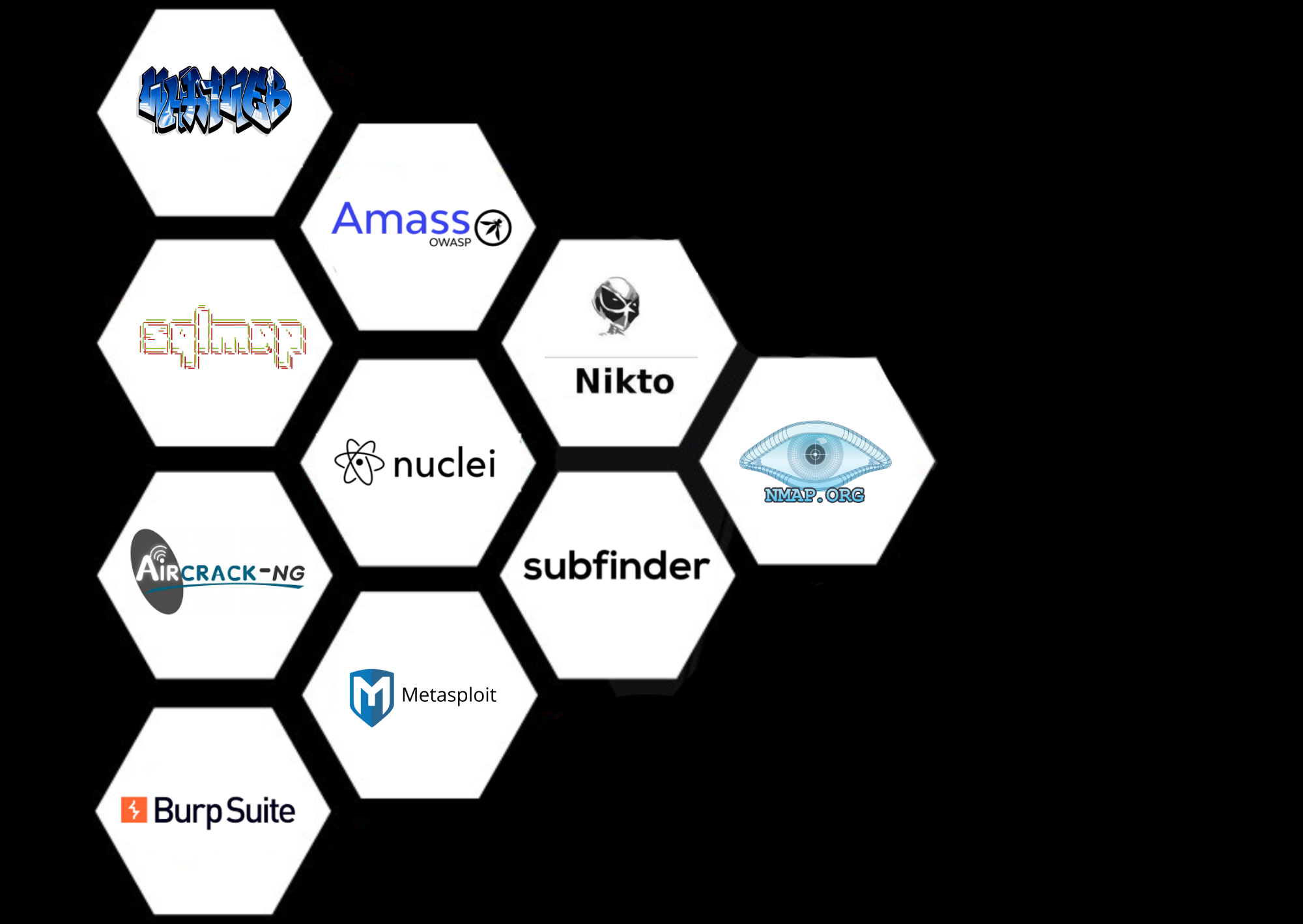
Tools Integrated
Nmap, Nikto, Subfinder, Amass, Nuclei, Gobuster, Metasploit, WhatWeb, HTTPProbe
Key Features
Role-based access control (Admin/Non-Admin)
PDF reporting for professional documentation
Live exploit monitoring dashboard
Modular design for scalability and customization
Use Case
Used internally to simulate red team workflows in a controlled, repeatable, and auditable format.
Recon Automation Scripts
Enumeration Framework
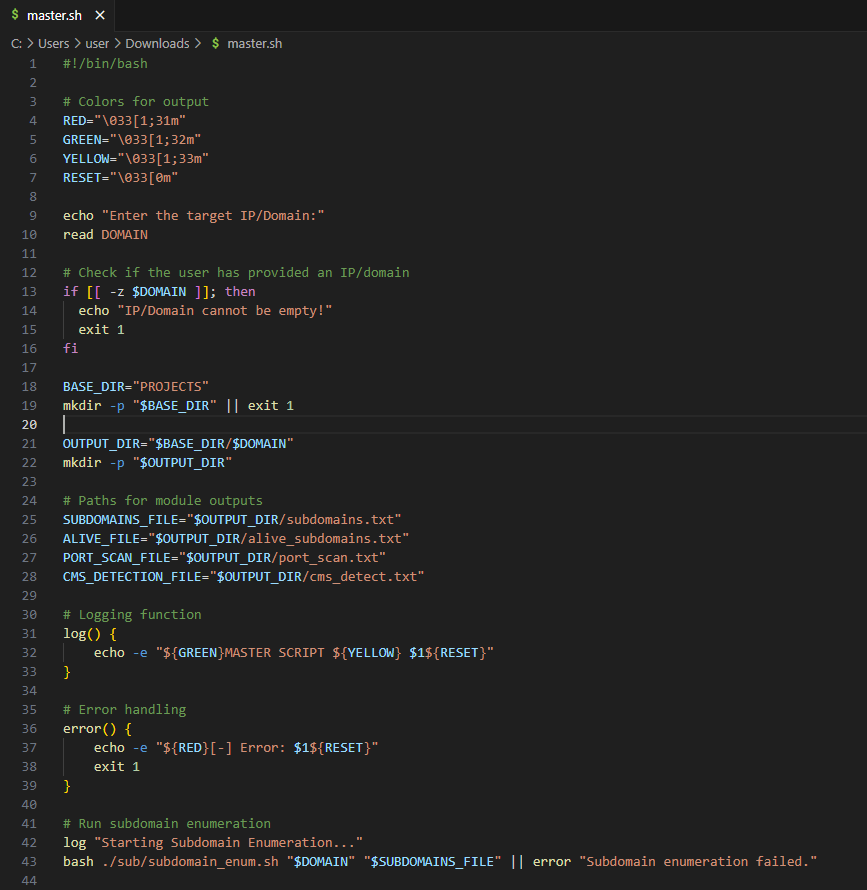
A fully automated reconnaissance framework built in Bash, designed to streamline red team infrastructure enumeration.
Tools Integrated
Assetfinder, Amass, Hydra, Smbclient, Gobuster, WhatWeb, Nmap, Nikto, HTTPProbe
Modules Included
master_enum.sh – master automation script
subdomain_enum.sh – subdomain discovery
alive_checker.sh – live host detection
port_scan.sh – port enumeration
cms_detection.sh – CMS identification
Key Achievements
Delivered up to 40% faster recon times compared to manual workflows during internal labs and test environments.
Coming Soon!
Red Team Labs

Hands-on, guided Active Directory and red team labs where you’ll practice real-world attacks in a safe environment.
From enumeration to privilege escalation and persistence, these labs will mirror modern adversary tactics and help you prepare for certifications and real operations.
Launching soon — stay tuned for early access!
Coming Soon!
Lab Setup Guides
Step-by-step guides to building your own cybersecurity lab from scratch.
Includes AD environments, vulnerable web apps, and cloud attack simulations — everything you need to practice offensive security the right way.
Coming soon — sign up to Encrypticle Weekly to get notified first.
3-Step Learning Path
Your 3-Step Path to Cybersecurity Skills
- 1
Learn with Tutorials 🎥
Step-by-step walkthroughs on Active Directory attacks, bug bounty exploits, and red team tactics.
- 2
Practice with Resources 🛠️
Download cheat sheets, scripts, and lab guides to practice on your own.
- 3
Apply & Grow 🚀
Use your skills in certifications, bug bounty programs, or red team projects.
Credentials & Proof
I’m Jagdeep Singh — a security researcher, red teamer, and bug bounty hunter. I hold CEH, PWPA, and CRTP certifications, and I’m ranked in the Top 4% globally on TryHackMe.
Through Encrypticle, I simplify advanced cybersecurity concepts into step-by-step tutorials, red team labs, and free resources that anyone can follow.
My mission is to help learners and professionals build real-world offensive security skills — from Active Directory attacks to bug bounty writeups — so they can grow their careers and defend against modern threats with confidence.

CRTP (Certified Red Team Professional)
Advanced Active Directory exploitation and red team certification, recognized as one of the best for practical AD attack skills.
CEH (Certified Ethical Hacker)
Industry-recognized certification covering penetration testing and ethical hacking fundamentals.
PWPA (Practical Web Pentest Associate)
Hands-on certification proving my ability to assess and exploit real-world web applications.
TryHackMe – Top 4%
Ranked among the top 4% of learners worldwide, highlighting consistent, practical lab performance
Work With Me
I provide focused, practical security help for learners and businesses.
- 1
Penetration Testing
Web, AD, and cloud security testing to uncover real vulnerabilities.
- 2
Bug Bounty Mentoring
Guidance on tools, workflows, and reporting to succeed in bug bounty.
- 3
Training & Workshops
Hands-on labs and sessions to build practical red team skills.
- 4
Speaking & Collaborations
Podcasts, conferences, and projects on offensive security.
